1
/
of
8
PayPal, credit cards. Download editable-PDF and invoice in 1 second!
GB/T 37374-2019 English PDF (GBT37374-2019)
GB/T 37374-2019 English PDF (GBT37374-2019)
Regular price
$155.00 USD
Regular price
Sale price
$155.00 USD
Unit price
/
per
Shipping calculated at checkout.
Couldn't load pickup availability
Delivery: 3 seconds. Download true-PDF + Invoice.
Get QUOTATION in 1-minute: Click GB/T 37374-2019
Historical versions: GB/T 37374-2019
Preview True-PDF (Reload/Scroll if blank)
GB/T 37374-2019: Intelligent transport -- Digital certificate application interface
GB/T 37374-2019
NATIONAL STANDARD OF THE
PEOPLE’S REPUBLIC OF CHINA
ICS 03.220.20; 35.240.60
R 07
Intelligent Transport -
Digital Certificate Application Interface
ISSUED ON: MAY 10, 2019
IMPLEMENTED ON: DECEMBER 01, 2019
Issued by: State Administration for Market Regulation;
Standardization Administration of PRC.
Table of Contents
Foreword ... 3
1 Scope ... 4
2 Normative References ... 4
3 Terms and Definitions ... 4
4 Abbreviations ... 5
5 Digital Certificate Application Interface ... 5
6 Security Message Syntax ... 12
Appendix A (Informative) Cooperative ITS Security Signature Message
Example ... 24
Appendix B (Informative) Cooperative ITS Security Encryption Message
Example ... 26
Bibliography ... 28
Intelligent Transport -
Digital Certificate Application Interface
1 Scope
This Standard specifies the digital certificate application interface and security
message syntax in the intelligent transport system.
This Standard is applicable to the design, research and development, and test of the
software and hardware systems related to the digital certificate applications in the
intelligent transport system.
2 Normative References
The following documents are essential to the application of this document. For the
dated documents, only the versions with the dates indicated are applicable to this
document; for the undated documents, only the latest version (including all the
amendments) are applicable to this document.
GB/T 25069-2010 Information Security Technology – Glossary
GM/T 0010 SM2 Cryptography Message Syntax Specification
3 Terms and Definitions
For the purpose of this document, the terms and definitions given in GB/T 25069-2010
and the following apply.
3.1 Intelligent transport system
In the more improved transport infrastructure, effectively and comprehensively use the
advanced science and technology (information technology, computer technology, data
communication technology, sensor technology, electronic control technology,
automatic control theory, operations research, artificial intelligence, etc.) into the fields
of transportation, service control, and vehicle manufacturing; strengthen the contact
among the vehicle, road and users; so that form a comprehensive transport system
that guarantees safety, increases efficiency, improved environment, and saves energy.
3.2 Cooperative ITS
An intelligent transport system that realizes intelligent coordination and cooperation
between vehicle and infrastructure, between vehicle and vehicle, between vehicle and
user through the information interaction of user, vehicle and road.
3.3 Digital certificate
A digital file containing public key owner information, public key, issuer information,
expiration date, and some extended information signed by the certification authority.
[GB/T 20518-2006, definition 3.7]
3.4 SM2 algorithm
An elliptic curve cryptographic algorithm with a key length of 256 bits.
3.5 Algorithm identifier
Digital information used to identify algorithmic mechanism.
4 Abbreviations
The following abbreviations are applicable to this document.
ASN.1: Abstract Syntax Notation One
OER: Octet Encoding Rules
ITS: Intelligent Transport System
UTC: Coordinated Universal Time
CBC: Cipher Block Chaining
CFB: Cipher Feedback
OFB: Output Feedback
CCM: Counter with Cipher Block Chaining-Message
5 Digital Certificate Application Interface
5.1 Overview
Digital certification application interface includes message signature and verification,
Description: verification of message digital signature
Parameters: plain [IN] signature original data buffer area pointer.
plainLen [IN] signature original data length.
signer [IN] encoded byte data buffer area pointer for the signer
certificate.
signerLen [IN] signature certificate data length.
pk [IN] verification public key in the signature certificate.
sign [IN] signature value.
Return value: 0 – success; other – verification failure.
5.5 Message asymmetric encryption
The message asymmetric encryption interface is defined as follows:
Description: conduct the data encryption on the message
Parameters: plain [IN] original text to be encrypted.
plainLen [IN] original text length.
symAlg [IN] symmetric encryption algorithm, defined as follows:
pk [IN] encrypted public key from the certificate or
signature message.
kek [OUT] the result of encrypting a randomly generated
symmetric key using an encrypted public key.
cipherText [OUT] symmetric encryption result.
Return value: 0 – encryption success; other – error.
Prototype:
The security message syntax structure can be divided into two types:
a) When the application certificate type indicates organization certificate, civil
service certificate, social public certificate, device certificate, the security
message syntax structure shall follow GM/T 0010;
b) When the application certificate type indicates ITS device certificate, the security
message syntax structure shall follow the definition of this Clause.
6.2 Description of basic elements
6.2.1 Encoding rules
The security message syntax consists of several types of basic elements. The
following basic element data structure and message syntax are described by using
ASN.1; and use OER to encode each information in the signature message and
encrypted message.
6.2.2 Basic data type
The basic data type is defined as follows:
6.2.3 3-byte hash value
The 3-byte hash value is defined as the Hashedld3 type; its structure is as follows:
Instruction: this hash value is used to identify the data such as certificates. Firstly,
calculate the hash value of the input data; taking the lower 3 bytes of the 32-byte hash
value.
6.2.4 8-byte hash value
The 8-byte hash value is defined as the Hashedld8 type; its structure is as follows:
Instruction: this hash value is used to identify the data such as certificates. Firstly,
Instruction: this structure represents a public key for asymmetric encryption calculation
and its supported symmetric cryptographic algorithm.
6.2.9 Encrypted symmetric key
The symmetric key for encryption is defined as EciesEncryptedKey type; its structure
is as follows:
Instruction:
eccCurve indicates the elliptic curve used for asymmetric cryptographic calculation;
Vector v: the temporary key used by the sender for encryption. This temporary key v
is used only once; each encryption shall generate new key;
Vector c: contains the encrypted symmetric key;
Vector t: when the public key encryption algorithm is the Chinese cipher algorithm, it
corresponds to the M in the Chinese cipher algorithm. When the public key encryption
algorithm is the international algorithm, it contains 16-byte authentication token, which
is placed in the first 16 bytes; the last 16 bytes are zero.
6.2.10 Signer information
The certificate signer information is defined as SignerInfo type, its structure is as
follows:
When not self-signing, it indicates the encoding content of the signer certificate.
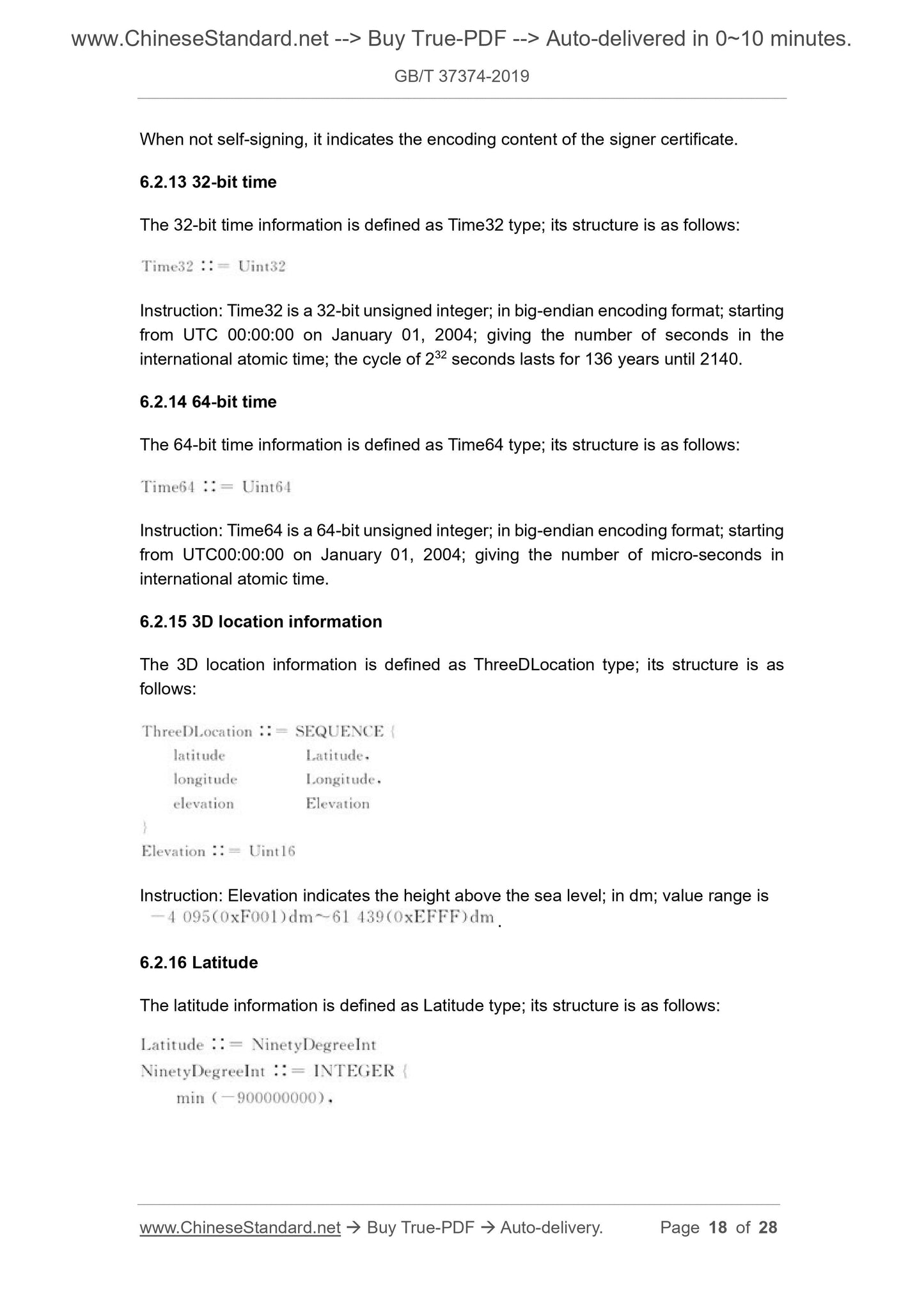
6.2.13 32-bit time
The 32-bit time information is defined as Time32 type; its structure is as follows:
Instruction: Time32 is a 32-bit unsigned integer; in big-endian encoding format; starting
from UTC 00:00:00 on January 01, 2004; giving the number of seconds in the
international atomic time; the cycle of 232 seconds lasts for 136 years until 2140.
6.2.14 64-bit time
The 64-bit time information is defin...
Get QUOTATION in 1-minute: Click GB/T 37374-2019
Historical versions: GB/T 37374-2019
Preview True-PDF (Reload/Scroll if blank)
GB/T 37374-2019: Intelligent transport -- Digital certificate application interface
GB/T 37374-2019
NATIONAL STANDARD OF THE
PEOPLE’S REPUBLIC OF CHINA
ICS 03.220.20; 35.240.60
R 07
Intelligent Transport -
Digital Certificate Application Interface
ISSUED ON: MAY 10, 2019
IMPLEMENTED ON: DECEMBER 01, 2019
Issued by: State Administration for Market Regulation;
Standardization Administration of PRC.
Table of Contents
Foreword ... 3
1 Scope ... 4
2 Normative References ... 4
3 Terms and Definitions ... 4
4 Abbreviations ... 5
5 Digital Certificate Application Interface ... 5
6 Security Message Syntax ... 12
Appendix A (Informative) Cooperative ITS Security Signature Message
Example ... 24
Appendix B (Informative) Cooperative ITS Security Encryption Message
Example ... 26
Bibliography ... 28
Intelligent Transport -
Digital Certificate Application Interface
1 Scope
This Standard specifies the digital certificate application interface and security
message syntax in the intelligent transport system.
This Standard is applicable to the design, research and development, and test of the
software and hardware systems related to the digital certificate applications in the
intelligent transport system.
2 Normative References
The following documents are essential to the application of this document. For the
dated documents, only the versions with the dates indicated are applicable to this
document; for the undated documents, only the latest version (including all the
amendments) are applicable to this document.
GB/T 25069-2010 Information Security Technology – Glossary
GM/T 0010 SM2 Cryptography Message Syntax Specification
3 Terms and Definitions
For the purpose of this document, the terms and definitions given in GB/T 25069-2010
and the following apply.
3.1 Intelligent transport system
In the more improved transport infrastructure, effectively and comprehensively use the
advanced science and technology (information technology, computer technology, data
communication technology, sensor technology, electronic control technology,
automatic control theory, operations research, artificial intelligence, etc.) into the fields
of transportation, service control, and vehicle manufacturing; strengthen the contact
among the vehicle, road and users; so that form a comprehensive transport system
that guarantees safety, increases efficiency, improved environment, and saves energy.
3.2 Cooperative ITS
An intelligent transport system that realizes intelligent coordination and cooperation
between vehicle and infrastructure, between vehicle and vehicle, between vehicle and
user through the information interaction of user, vehicle and road.
3.3 Digital certificate
A digital file containing public key owner information, public key, issuer information,
expiration date, and some extended information signed by the certification authority.
[GB/T 20518-2006, definition 3.7]
3.4 SM2 algorithm
An elliptic curve cryptographic algorithm with a key length of 256 bits.
3.5 Algorithm identifier
Digital information used to identify algorithmic mechanism.
4 Abbreviations
The following abbreviations are applicable to this document.
ASN.1: Abstract Syntax Notation One
OER: Octet Encoding Rules
ITS: Intelligent Transport System
UTC: Coordinated Universal Time
CBC: Cipher Block Chaining
CFB: Cipher Feedback
OFB: Output Feedback
CCM: Counter with Cipher Block Chaining-Message
5 Digital Certificate Application Interface
5.1 Overview
Digital certification application interface includes message signature and verification,
Description: verification of message digital signature
Parameters: plain [IN] signature original data buffer area pointer.
plainLen [IN] signature original data length.
signer [IN] encoded byte data buffer area pointer for the signer
certificate.
signerLen [IN] signature certificate data length.
pk [IN] verification public key in the signature certificate.
sign [IN] signature value.
Return value: 0 – success; other – verification failure.
5.5 Message asymmetric encryption
The message asymmetric encryption interface is defined as follows:
Description: conduct the data encryption on the message
Parameters: plain [IN] original text to be encrypted.
plainLen [IN] original text length.
symAlg [IN] symmetric encryption algorithm, defined as follows:
pk [IN] encrypted public key from the certificate or
signature message.
kek [OUT] the result of encrypting a randomly generated
symmetric key using an encrypted public key.
cipherText [OUT] symmetric encryption result.
Return value: 0 – encryption success; other – error.
Prototype:
The security message syntax structure can be divided into two types:
a) When the application certificate type indicates organization certificate, civil
service certificate, social public certificate, device certificate, the security
message syntax structure shall follow GM/T 0010;
b) When the application certificate type indicates ITS device certificate, the security
message syntax structure shall follow the definition of this Clause.
6.2 Description of basic elements
6.2.1 Encoding rules
The security message syntax consists of several types of basic elements. The
following basic element data structure and message syntax are described by using
ASN.1; and use OER to encode each information in the signature message and
encrypted message.
6.2.2 Basic data type
The basic data type is defined as follows:
6.2.3 3-byte hash value
The 3-byte hash value is defined as the Hashedld3 type; its structure is as follows:
Instruction: this hash value is used to identify the data such as certificates. Firstly,
calculate the hash value of the input data; taking the lower 3 bytes of the 32-byte hash
value.
6.2.4 8-byte hash value
The 8-byte hash value is defined as the Hashedld8 type; its structure is as follows:
Instruction: this hash value is used to identify the data such as certificates. Firstly,
Instruction: this structure represents a public key for asymmetric encryption calculation
and its supported symmetric cryptographic algorithm.
6.2.9 Encrypted symmetric key
The symmetric key for encryption is defined as EciesEncryptedKey type; its structure
is as follows:
Instruction:
eccCurve indicates the elliptic curve used for asymmetric cryptographic calculation;
Vector v: the temporary key used by the sender for encryption. This temporary key v
is used only once; each encryption shall generate new key;
Vector c: contains the encrypted symmetric key;
Vector t: when the public key encryption algorithm is the Chinese cipher algorithm, it
corresponds to the M in the Chinese cipher algorithm. When the public key encryption
algorithm is the international algorithm, it contains 16-byte authentication token, which
is placed in the first 16 bytes; the last 16 bytes are zero.
6.2.10 Signer information
The certificate signer information is defined as SignerInfo type, its structure is as
follows:
When not self-signing, it indicates the encoding content of the signer certificate.
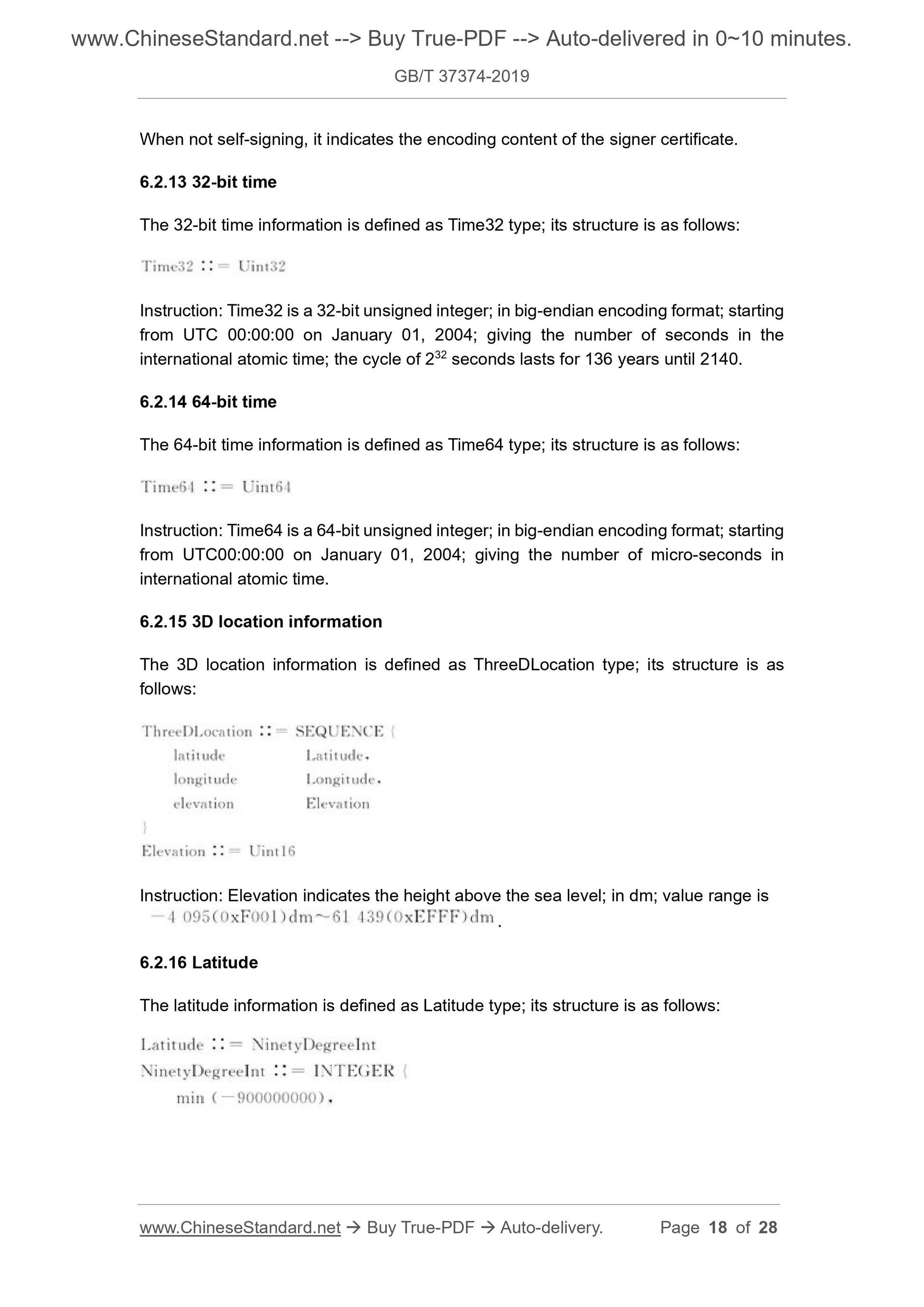
6.2.13 32-bit time
The 32-bit time information is defined as Time32 type; its structure is as follows:
Instruction: Time32 is a 32-bit unsigned integer; in big-endian encoding format; starting
from UTC 00:00:00 on January 01, 2004; giving the number of seconds in the
international atomic time; the cycle of 232 seconds lasts for 136 years until 2140.
6.2.14 64-bit time
The 64-bit time information is defin...
Share